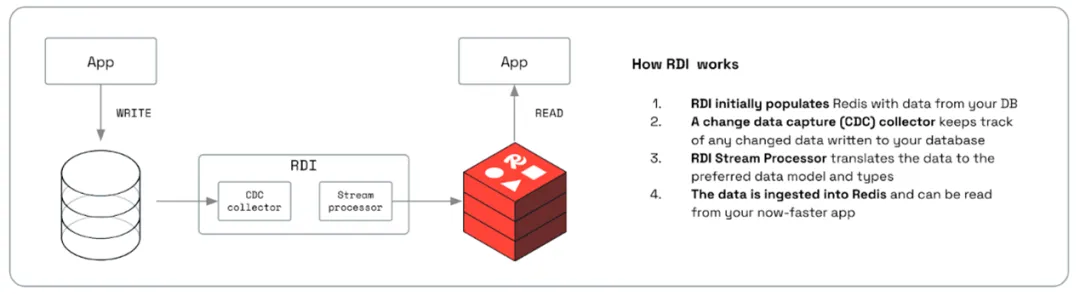
Hongke Redis: Data Management Upgrade! RDI helps you realize real-time data synchronization without deviation.
HongKe's latest articles HongKe [HongKe Redis]: Data Management Upgrade! RDI helps you achieve real-time data synchronization without bias Introduction: We are not only committed to accelerating the process of building applications, but also focusing on helping you achieve your ultimate goals.



2-1-300x200-1.jpg)




