- Home
- Technical Products
Enterprise Cloud IT Solutions
Test Measurement
Industrial Measurement
- Solutions
Enterprise Cloud IT Solutions
Test Measurement
- Latest Articles
- About Us
 EN
EN
Case Study & News
Latest Articles
Hong Kong Hongke Application & News


Hongke Case
How Domo BI creates 500%+ ROI, the intelligent decision-making strategy of the world's top data teams
Read More " November 27, 2025

Hongke Case
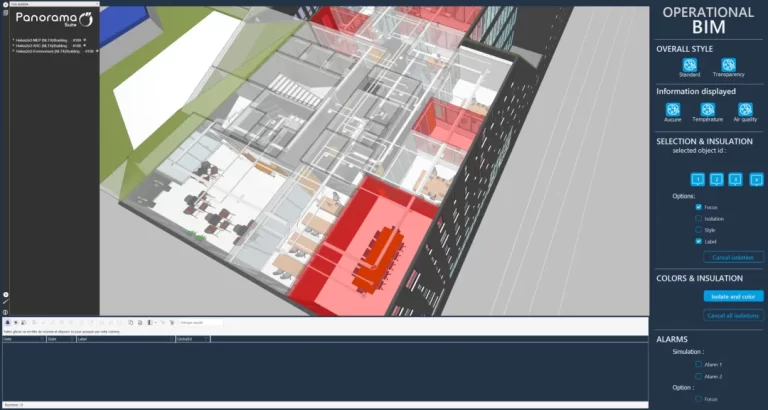
How to Identify Invisible Energy Wastage in Buildings - Panorama Intelligent Energy Management
Read More " December 3, 2025


Hongke Case
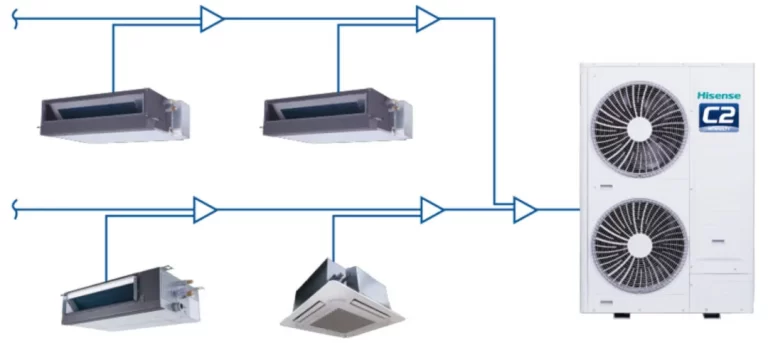
Hongke Solutions] Embedded AI Rise: How CAN Buses Reinvent Real-Time Control and Edge Intelligence?
Read More " December 10, 2025


Hongke Case
HONGKE Solutions] HONGKE GNSS Simulator - Faster, More Accurate and Repeatable Inspection Drone Testing
Read More " December 5, 2025


Hongke Dynamic
HONGKONG NEWS] CEO CHAN CHAU-YUEN ATTENDED 25th ANNIVERSARY GALA OF THE HONG KONG CHAMBER OF COMMERCE IN GOVERNMENT.
Read More " December 15, 2025


Hongke Dynamic
HongKong News] KnowBe4 Ranked as 2026 GSV Top 150: Leading Security Awareness Training and Phishing Protection in the AI Era
Read More " November 14, 2025