- Home
- Technical Products
Enterprise Cloud IT Solutions
Test Measurement
Industrial Measurement
- Solutions
Enterprise Cloud IT Solutions
Test Measurement
- Latest Articles
- About Us
 EN
EN
Lepide Data Security Management Platform
Cataloging and Data Security Made Simple
Simple and cost-effective way to achieve comprehensive audit and protection of files/folders and their access control systems.
Sensitive Unstructured Data Protection Solution Trusted by 1,000+ Businesses Worldwide








Data security and compliance should be simple and efficient.
Lepide provides the industry's most cost-effective data security solution.
Easy to deploy, powerful protection. Unlike other vendors, we provide enterprise-grade security through AI-driven audit reports, privilege analysis, and real-time threat remediation without enterprise-grade costs. The choice of more than 1,000 organizations worldwide, Lepide combines cutting-edge technology with intuitive ease-of-use to help you stay on top of risk and compliance requirements.

Stay on top of your data and Active Directory in real time.

Intelligently analyze permissions and block abnormal access immediately.

Real-time threat alerts for accelerated security response
Functions

Enhancing Data Security Situation Management
Reduce the attack surface and minimize risk by integrating data visibility, access control, threat detection and classification into one platform.

Prevent data leakage and security threats
Discover and respond to security threats instantly with automated real-time threat detection, user behavior analysis and threat response processes.

Achieving and Maintaining Compliance
Hundreds of predefined compliance reports, data categorization features, and proactive auditing, monitoring and alerting ensure that Lepide meets multiple compliance requirements.
Detecting, preventing and responding to data breaches
Lepide helps organizations effectively prevent, detect and respond to data breaches by limiting threat exposure, identifying over-authorized users, scanning for over-exposed data, and using threat models to detect anomalous behavior in real time. It also supports rapid investigation of the cause of a breach, identifies affected data and intrusion paths, and provides immediate response.
Data Loss Prevention (DLP)
Protect your sensitive information from data leakage with Lepide's advanced data loss prevention solutions. Detect, monitor and protect valuable data from unauthorized access or accidental loss, ensuring the security and integrity of your company's critical assets.
DSPM (Data Security Situation Management) gives you complete visibility into the location, access and utilization of sensitive data and the security status of your storage environment. With Lepide, you can easily deploy a complete DSPM solution.
Lepide Artificial Intelligence Security
AI tools such as Copilot can boost productivity by making efficient use of data and optimizing content creation methods. However, many organizations are not yet ready to fully adopt AI technology due to security and privacy concerns. That's where Lepide comes in.
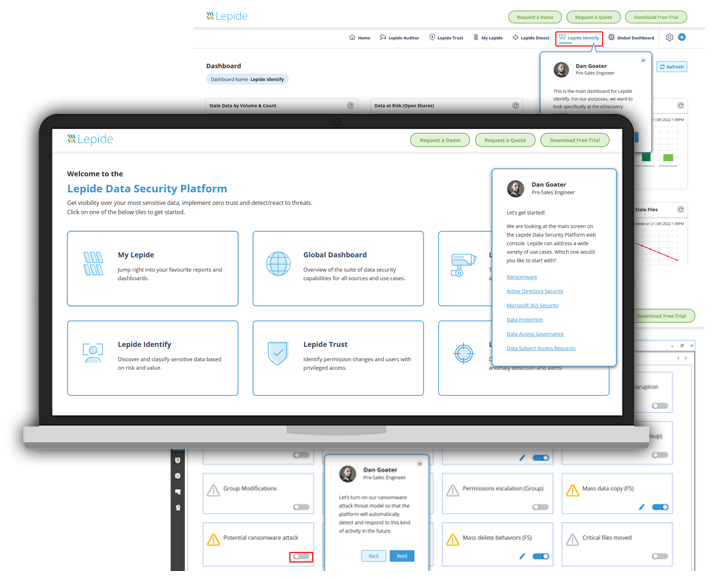
Want to learn how the Lepide platform actually works?
Take a virtual tour of the Lepide Data Security Platform in our online demo. Learn how Lepide can meet your needs for ransomware protection, Active Directory security, Microsoft 365 security, data protection, data access governance, and many other application scenarios.
Safety Tools for Getting Out of Isolation
Preventing data leakage isn't complicated. Understand your sensitive data, visualize permission settings, and analyze user behavior for potential threat indicators.
Lepide provides all the answers you need to confidently tackle security challenges in a clear, accurate context
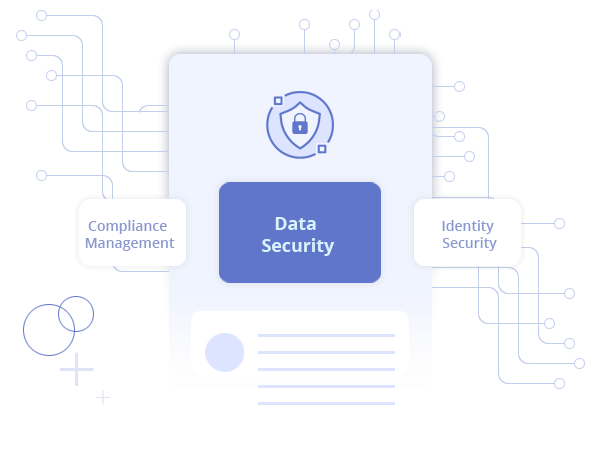
Data Security
Data is like a gold mine, a target for attackers. Lepide helps you locate sensitive data, see who has access, understand how data is used, and monitor user activity to detect suspicious behavior.
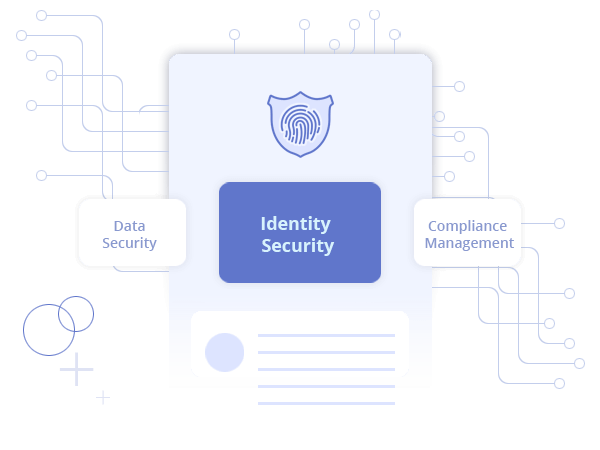
identity security
Privileged users hold the "key" to the system. Lepide helps you identify privileged users, see how their permissions are assigned, find out which users are overprivileged, and track when permissions are changed.
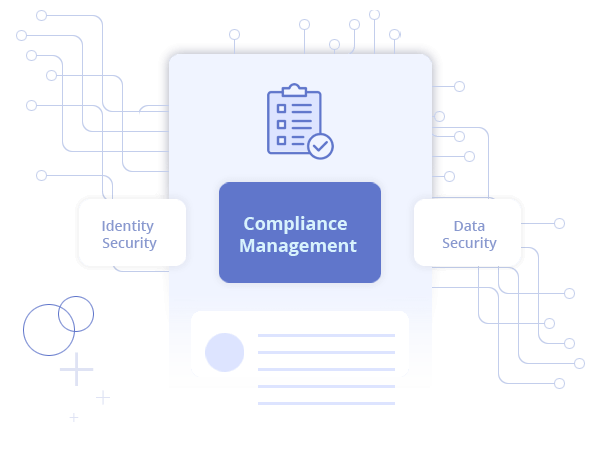
Compliance Management
Lepide provides a proven framework to help you achieve and maintain compliance by identifying, protecting, detecting, responding and recovering.
Suitable for a wide range of scenarios

artificial intelligence security

Data Security Situation Management

Data leakage

Data Loss Prevention

Ransomware Protection

Compliance Management

Active Directory Security

Data Access Governance

Cloud Data Security
Adopting a proven success framework
Enhancing data security and preventing threats requires a proven approach.
The Lepide Safety Framework is field-proven, reliable and reusable.
Recognition
Data Confirmation
Classification
power analysis (math.)
Protection
Threat Reduction
AD Security Management
Data Security
Detection
User Behavior Analysis
Change Audit and Reporting
Threat Detection Workflow
Response
Real-time Alerts
Automatic Threat Response
Mobile Apps
recover (health, economic)
Detailed Audit Log
Incident Analysis
Root cause determination
Full coverage of your local, cloud or hybrid environment

Office 365

file server

Share Point

Active Directory

SQL Server

Exchange

NetApp

Amazon S3

G Suite

More...
Explanation of Lepide Data Security Platform Architecture
Audit and Reporting
Reduce the threat surface by identifying overexposed data, discovering configuration errors and auditing changes with Lepide Auditor.
Access Governance
With Lepide Trust, you can check the access rights of sensitive data, identify users with excessive rights, and control data access in a unified way.
Threat Detection
Identify and respond to threats instantly with Lepide Detect anomaly detection, alerts, threat modeling and automated threat response.
Classification
With Lepide Identify, locate where the most sensitive unstructured data is stored and categorize it as soon as it is created.
Rights Management
Implement zero-trust security by removing redundant permissions with Lepide Protect.
AI Security Assistant
Rapidly analyze data with Lepide IQ's AI Assistant to ensure your organization remains agile and accelerates decision-making.
User Cases
Western Connecticut Medical Network
Lepide was easy to use and effective right off the bat. In addition, their patience, care, and technical knowledge far exceeds that of most support and sales teams I've seen before.
Drayke Jackson
safety engineer

Edinburgh Napier University
We chose Lepide because they were able to provide us with threat detection and response, and segregate reporting duties to a web console, all on one platform.
Kevin Gallagher
Senior Systems Administrator

Western Connecticut Medical Network
Lepide is a perfect fit for our IT security and compliance requirements. It has helped us reduce a lot of wasted time and money, and now we know we can comply with industry standards.
Agnel Dsilva
Information Technology Manager

Professional technical support from HONGKEI to help you succeed in your project.
As a provider specializing in enterprise cloud IT solutions and an official authorized Lepide reseller, Avision is committed to providing you with a series of paid technical services related to the product, aiming to help you succeed in your project in the most cost-effective way. If you are in need of Lepide's technical services, please contact us!

