- Home
- Technical Products
Enterprise Cloud IT Solutions
Test Measurement
Industrial Measurement
- Solutions
Enterprise Cloud IT Solutions
Test Measurement
- Latest Articles
- About Us
 EN
EN
HONGKE Lepide Data Security Governance Platform
Ransomware Protection
With Lepide data classification software, you can get a clearer picture of the contents of your documents.
Automatically scans and categorizes data related to PII, PHI, PCI, IP and other regulations.
Data Security and Threat Detection for 1000+ Companies

Data Security and Threat Detection for 1000+ Companies
Comprehensive Ransomware Protection Solution
Our focus is to provide you with visibility into the state of your data. With visibility, you can protect against ransomware attacks, detect ransomware symptoms in real time, and respond automatically.

Reduced attack surface
A true ransomware protection solution includes ensuring that you can identify and mitigate vulnerabilities in your overall security posture.

Detecting Ransomware Attacks
Discover early signs of a ransomware attack in progress with threshold alerts and out-of-the-box threat models/workflows.

Response and Recovery
Enable automated threat response to mitigate damage and use our detailed audit logs to help speed up investigation and recovery.
Want to know how it actually works?
Take a virtual tour of the Lepide data security platform in our web-based demo. Learn how Lepide fits your use case, whether it's ransomware, Active Directory security, Microsoft 365 security, data protection, data access governance or more.
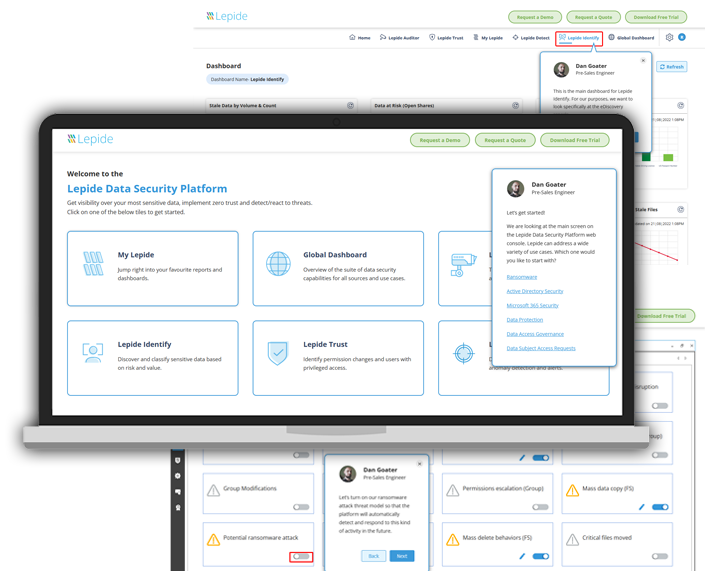
Protecting Against Ransomware Starts at the Attack Surface
While it's impossible to completely avoid ransomware attacks, you can reduce your risk of becoming a victim by identifying and remediating vulnerabilities in your security posture to minimize the attack surface. Lepide ransomware protection solutions can help you achieve this goal.
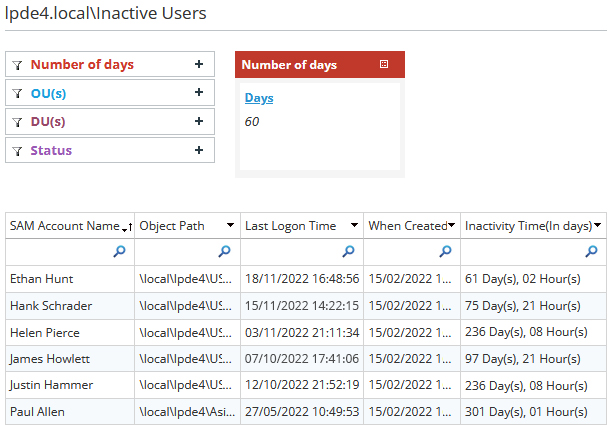
Identify and Deactivate Inactive Users
Inactive users are often forgotten or ignored, making them prime targets for cybercriminals looking to unleash ransomware. Obtaining reports on inactive users and knowing when they are inactive can help reduce the number of potential accounts that could be vulnerable to ransomware attacks.
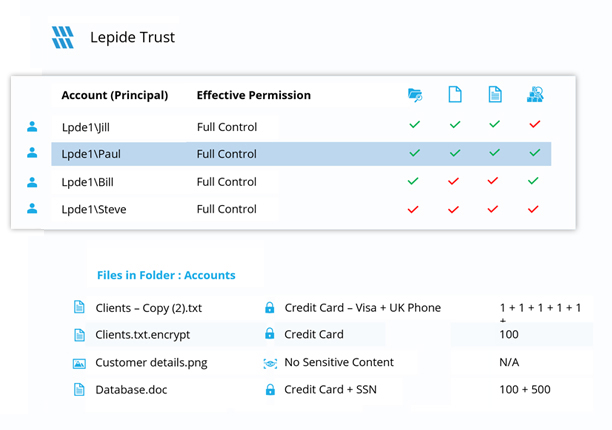
Overprivileged users
If users access sensitive data when they don't need to, it can increase the number of accounts and, if compromised, spread ransomware to your most valuable data. Lepide identifies users with excessive privileges based on how they access data.
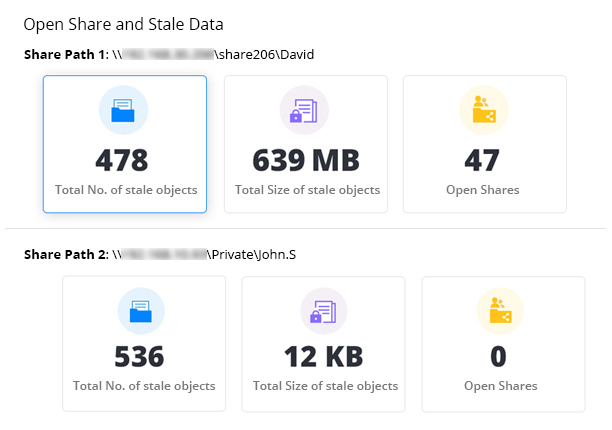
Open Shared Space
Most or all users on a given network can access data in open shares. If there is sensitive data in an open share, it can be affected whenever any user is attacked by ransomware. Lepide can help you minimize this exposure by providing you with a list of all open shares.
Most ransomware variants can be detected in your on-premise and cloud environments as they generate events that are signs of an ongoing attack. With Lepide, you can instantly detectransomwareThe spread.
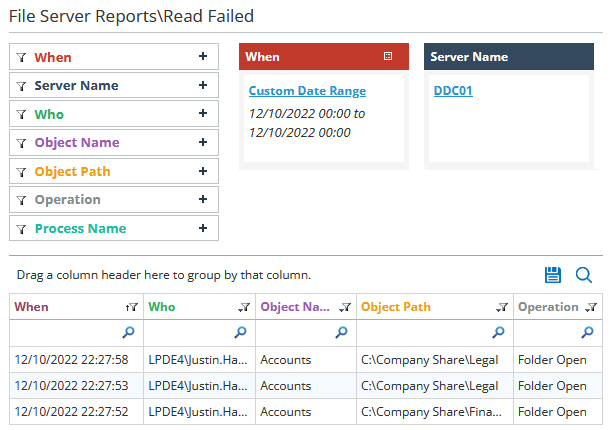
Detecting Failed Reads
A large number of file read failures indicates that a user's account may have been compromised by ransomware. Lepide reports file read failures in real-time and provides powerful search, sorting and filtering features to speed up and improve the accuracy of your investigation.
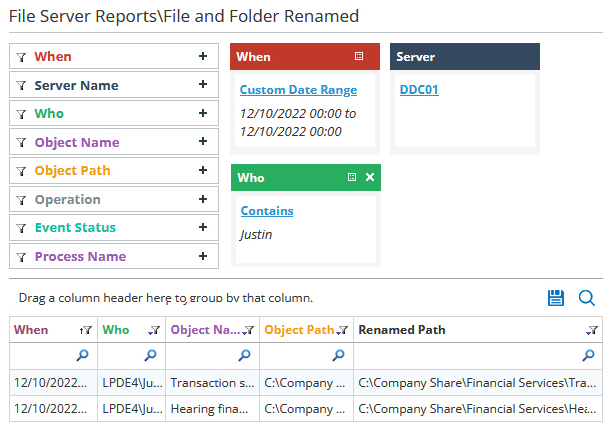
Identifying Renamed Files
Ransomware attacks often rename files, for example by adding file extensions. A large number of file renames in a short period of time may indicate a ransomware attack. With Lepide, you can detect these events in real time with dedicated reports.
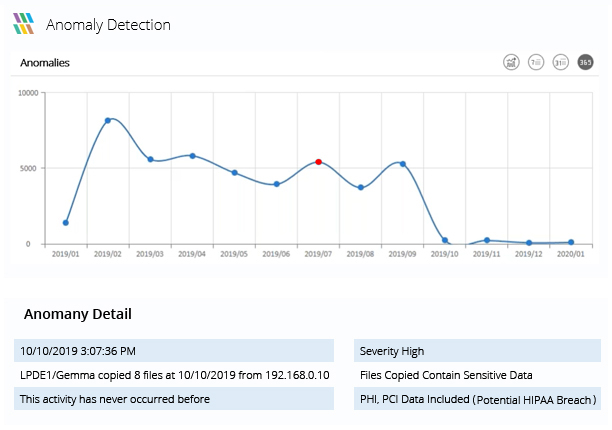
Identify changes in user behavior
If a user's account is compromised by ransomware, their behavior with data is likely to be different. With Lepide, you can automatically detect any anomalies in user behavior in real time. Alerts can be sent to your email or to the Lepide app.
Real-time Response to Ransomware Attacks
Once symptoms of a ransomware attack are detected, Lepide ransomware protection software automatically takes action, allowing you to make faster and more accurate investigation and recovery decisions.
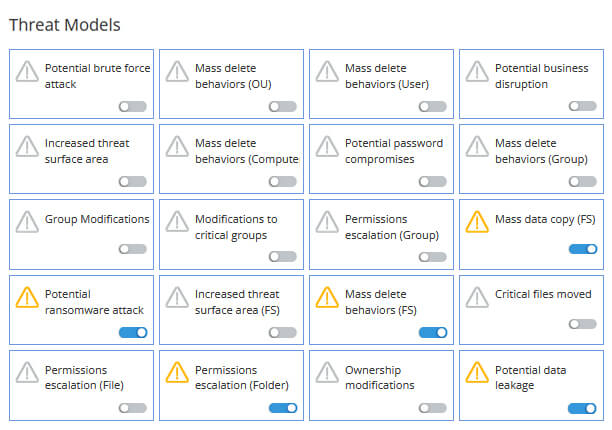
Dedicated Ransomware Threat Models
Turn on our ransomware threat model to automatically detect and respond to ransomware. When the threat model detects ransomware symptoms, it sends real-time alerts and executes customized responses to shut down infected user accounts, computers, or more.
Recognizing Potential Damage
Lepide's ransomware protection software discovers and categorizes sensitive data at the point of creation. With our detailed audit reports, you can pinpoint exactly what data is associated with threatened files and folders.
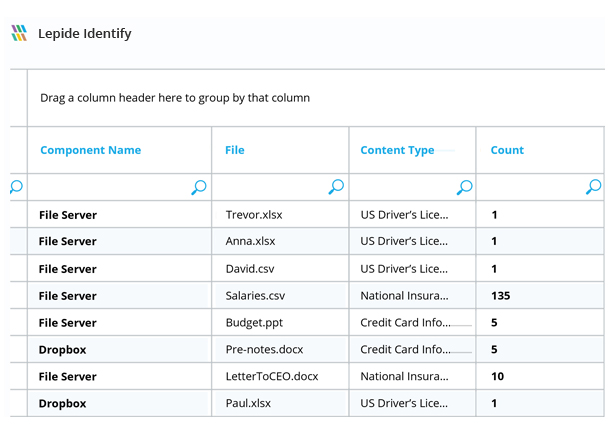
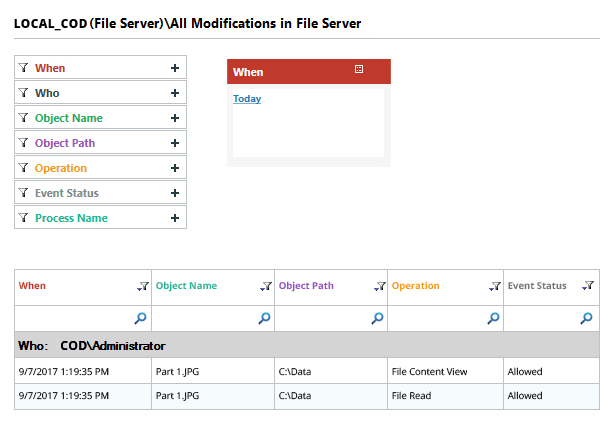
Confidence Report
With Lepide's detailed audit logs and simplified reporting views, you can extract the all-important "who," "what," "when," and "where" information for every event that occurs during a ransomware attack, giving you the visibility you need for accurate incident response reporting. "and where" information for each event that occurs during a ransomware attack, giving you the visibility you need for accurate incident response reporting.
Learn about the Lepide Data Security Platform
How to align with your ransomware prevention program
Success Stories
Western Connecticut Medical Network
Lepide was easy to use and effective right off the bat. In addition, their patience, care, and technical knowledge far exceeds that of most support and sales teams I've seen before.
- List Item #1
- List Item #1
- List Item #1
- List Item #1
- List Item #1

Drayke Jackson
Safety Engineer
Edinburgh Napier University
We chose Lepide because they were able to provide us with threat detection and response, and segregate reporting duties to a web console, all on one platform.
- List Item #1
- List Item #1
- List Item #1
- List Item #1
- List Item #1

Kevin Gallagher
Senior Systems Administrator
Danville
Lepide is a perfect fit for our IT security and compliance requirements. It has helped us reduce a lot of wasted time and money, and now we know we can comply with industry standards.
- List Item #1
- List Item #1
- List Item #1
- List Item #1
- List Item #1

Agnel Dsilva
Information Technology Manager

