
【虹科方案】從被動防禦到主動預防:用 KnowBe4 輕鬆應對關鍵基礎設施條例風險評估與審核
KnowBe4 為企業應對香港《關鍵基礎設施保護條例》提供了化繁為簡的解決方案。面對第 24 條與第 25 條的嚴格挑戰,它將難以量化的「人為風險」轉變為可追蹤的實戰數據,不僅彌補了傳統評估的盲點,更為年度審核提供了證明控制措施「有效運作」的鐵證。透過自動化報告與持續演練,企業能在大幅降低安全風險的同時,輕鬆滿足監管要求,實現從「被動合規」到「主動防禦」的關鍵轉型。
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Phishing attacks and ransomware are posing an ongoing threat to enterprise information security in a lower-cost, higher-revenue manner. From email baiting to double ransom, from vulnerability exploits to social engineering traps, traditional defenses are being challenged to the limit.
This article systematically comprehends the current threat landscape of enterprise cybersecurity, and details the role of enterprises in theMultifactor Authentication (MFA),Vulnerability Management,Cloud Backup,Mail Protectionbest practices in areas such as With a special focus on KnowBe4 How to do it throughSimulated Fishing Training,Behavioral AnalysisandSafety CultureIn order to create a "people"-focused security defense line, we help organizations to truly realize the "last mile" of information security.
Phishing is a typical social engineering attack that entices victims to provide sensitive information or perform malicious actions. Common methods include:
Fake links in emails or text messages
False Identity Interaction on Social Platforms
Create a sense of urgency by utilizing current events (e.g., epidemics, tax periods).
Most of them are aimed at account theft, malware implantation or subsequent ransom attacks.
Ransomware attacks are usually premised on infiltration, and common methods include:
Remote Desktop Protocol (RDP) configuration is not appropriate.
Malicious attachments to fishing emails
Software update channel hijacked
Social engineering induces the installation of malicious programs
Modern ransomware generally adopts the "double ransom" model:Encrypt the data, then threaten to leak it for a higher return.
According to the White Paper survey, organizations in the 74% consider MFA to be one of the most effective techniques for preventing phishing attacks.
MFA upgrades the verification from "knowing something" (password) to "owning something" (device) or "being someone" (biometrics), dramatically reducing the risk of password theft, i.e., intrusion.
Suggested Prioritization:
FIDO2 Hardware Key > Biometrics > TOTP Application > SMS or Email Authentication Code
One of KnowBe4's core services is to help organizations build an "Employee Safety Immunity System".
Effective training should cover:
Tips for recognizing phishing emails, business email scams (BEC), and social engineering traps
Design simulation exercises for high-risk positions (e.g. finance, personnel)
Quantify employee response through periodic phishing tests to track improvement results.
About 36% organizations were able to patch the vulnerability within hours after it was made public, but 20% took more than a couple of weeks, leaving hackers with an opportunity to exploit the vulnerability.
Businesses should be established:
Automated Patch Management System
Zero-Day Defense and Intrusion Prevention (IPS) capabilities
Isolation of legacy systems and application layer security protection
Properly configured email validation mechanisms can effectively reduce domain spoofing and phishing emails. The best results are achieved when all three are used in conjunction:
SPF: Defining a Trusted Outgoing Mail Server
DKIM: Ensure that the contents of the email have not been tampered with
DMARC: Develop a strategy for suspicious mail (quarantine or reject)
Cloud Security Demand Continues to Rise as Remote Work Gains Popularity. The White Paper shows:
More and more companies are deploying Cloud Native Security Services(e.g. CASB, EDR/XDR)
adopt AI/Machine Learning (ML) Automated detection and response
Through Hosted Security Services (MSSP) Responding to high-intensity attacks
More than 60% organizations consider offline or cloud backups to be a critical measure against ransomware.
Effective backup strategies should include:
Regular and complete data snapshots
Backups are stored offline to prevent simultaneous encryption.
Regular rehearsal of the recovery process to ensure RTO/RPO control
As technological defenses become more sophisticated, attackers are beginning to exploit human weaknesses as a breakthrough.
KnowBe4 Through the systematic "Security Awareness Training + Simulation Exercise" system, we help enterprises to enhance employees' defensive instincts, make up for the shortcomings of "human defense", and reduce the occurrence of phishing and extortion incidents from the source.
Focus on the root cause and not the symptoms: Build a first line of defense, starting with email security and identity authentication.
Cultural orientation: Encourage employees to take the initiative to ask questions and develop a corporate culture of "everyone participates in safety".
human-machine collaborationThe concept of "People are the last line of defense", as advocated by KnowBe4, makes safety start from awareness.
Active testing and rehearsal: Early detection of vulnerabilities through red team simulations and phishing tests.
Preparedness: Establish a mechanism for collaborative planning with MSSP, law enforcement, and legal counsel.
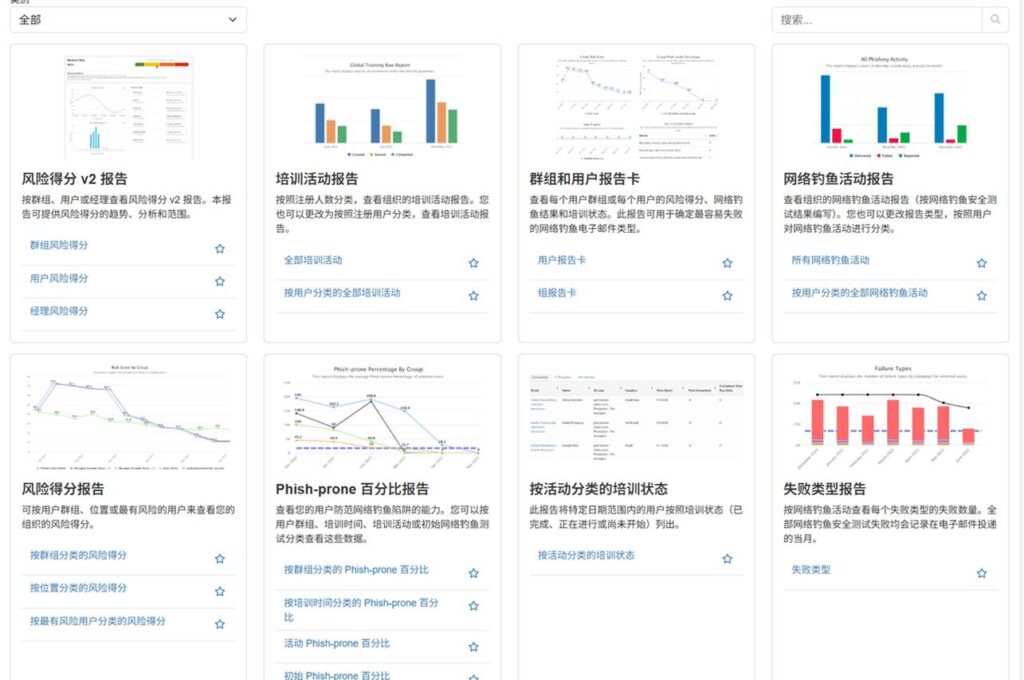
Real-world simulation training
Provides the world's largest phishing email simulation platform, allowing employees to learn to recognize threats in a secure environment and quantify improvements through "click-through" data.
Personalized Safety Training
Designed for different positions (e.g. finance, HR, management), the specialized courses cover phishing prevention, ransom defense, password security and social engineering identification.
Behavior-driven risk management
The system creates a "risk profile" based on employee behavior (clicks, returns, completion) and automatically configures enhanced policies (e.g., mandatory MFA, permission control) for high-risk users.
Safety Culture
Through security tips, quarterly challenges and positive incentives, we are gradually fostering a culture of "everyone is responsible for security" to reduce the space for social engineering attacks.
Phishing and ransom threats don't go away on their own, but continue to spread as attack thresholds are lowered and revenues are raised.
A New Type of Security Awareness Training by KnowBe4 It is the key to cracking the "human loophole".
By combining multi-factor authentication, automated detection, security culture building, and technological defense, enterprises can build a secure environment in an uncertain network environment.Firmware Defense SystemThe
Let security start with every employee, let defense become part of the corporate culture, and work with KnowBe4 to build an impenetrable "people + technology" information security line.

KnowBe4 為企業應對香港《關鍵基礎設施保護條例》提供了化繁為簡的解決方案。面對第 24 條與第 25 條的嚴格挑戰,它將難以量化的「人為風險」轉變為可追蹤的實戰數據,不僅彌補了傳統評估的盲點,更為年度審核提供了證明控制措施「有效運作」的鐵證。透過自動化報告與持續演練,企業能在大幅降低安全風險的同時,輕鬆滿足監管要求,實現從「被動合規」到「主動防禦」的關鍵轉型。

安鵬精密於實際 NVH 路測中,透過虹科 PCAN-MicroMod FD,將車輛 CAN / CAN FD 訊號即時轉換為類比電壓,無需二次開發即可完成訊號同步,低成本整合既有 NVH 資料採集系統。
虹科結合 AR 智慧眼鏡與 AI 辨識技術,打造標準化 PCB 質檢工作流程,整合 MES、ERP、AOI 系統,降低漏檢率、提升良率,加速電子製造數位化升級。